Deceptive design Audit Protocol.
I created the Deceptive Design Audit Protocol to systematically detect and prevent dark patterns that undermine transparency, choice, and user control. The audit gives teams a clear, repeatable checklist to evaluate flows against Privacy by Design principles—surfacing risks early, before they ship. It helps align product, legal, and design on compliant defaults, plain-language disclosures, and easy consent/revocation. By operationalizing these checks, the protocol reduces regulatory exposure, improves data quality, and—most importantly—builds user trust at scale.
Basis
Designers have an ethical duty to create experiences that respect user agency while operating within existing legal frameworks. Because teams control critical aspects of the user journey, they can unintentionally (or intentionally) introduce dark patterns—now frequently cited in litigation and regulatory actions. This protocol grounds design decisions in evidence and law, helping teams avoid deceptive tactics, reduce risk, and uphold Privacy by Design principles.
Foundation
This foundation synthesizes established deceptive-design taxonomies (e.g., “dark patterns” from HCI/UX research), consumer-protection guidance and enforcement trends (FTC, EU), and classic usability heuristics. I translated recurring risk areas—like comparison prevention, confirmshaming, fake scarcity/urgency, sneakiness, and obstruction—into clear checks a product team can apply to real flows. The result is an evidence-informed audit that maps known deception patterns to practical tests, so teams can spot issues early, reduce regulatory risk, and protect user agency.
Where To Begin
Start with a complete, end-to-end journey—one task from first touch to completion. Good candidates: sign-up → use → cancellation or consent opt-in → manage → opt-out. Map every screen, state, and decision point, then assess each step for deceptive patterns, clarity of language, default choices, disclosure timing, and ease of reversal (e.g., cancel, revoke). Crucially, include the behind-the-scenes workflow (systems, rules, fees, data flows) so auditors can detect asymmetry, hidden costs, sneaking, and privacy-zuckering.
Tagging Scheme
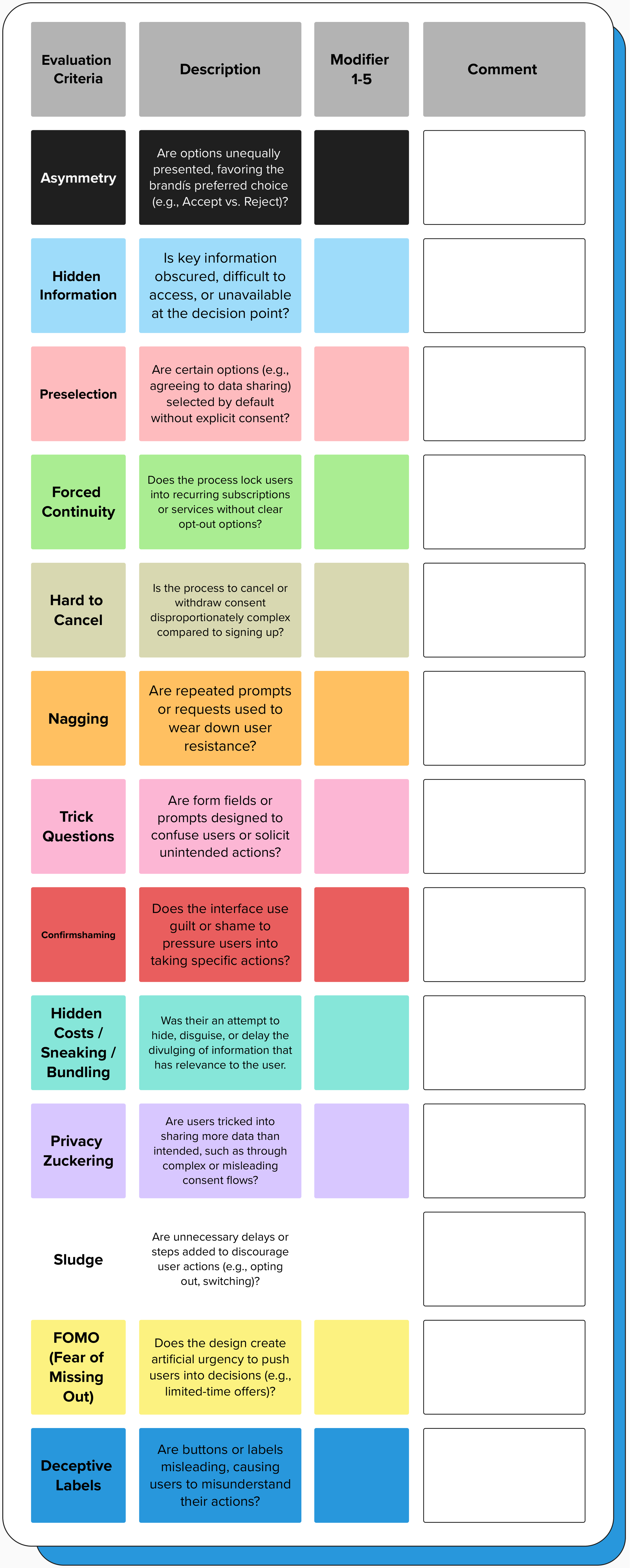
Next: Tagging by Established Dark Patterns
This audit uses a tagging scheme mapped to well-documented deceptive design patterns (e.g., preselection, confirmshaming, hidden costs, sludge) so issues can be labeled consistently, compared across flows, and tracked over time.
Color-coding makes it easy to spot the most common patterns in the design and where risk clusters.
When the audit is complete, the output should look like this.
Once the experience is tagged, you’ll have a prioritized backlog to review and resolve with your product, legal, and engineering teams.